Today’s businesses need quick network computer access for teamwork. Sharing files and resources is key for work in offices and from home.
This shared resources guide will teach you the basics of network sharing. It’s useful for accessing project files or sharing printers. Learning these skills can really help your team.
Setting it up right means safe and steady access to company data. It keeps your information safe and helps your team work better together.
Our tips will show you how to connect to shared folders and other network resources. This skill helps teams work faster and keeps important business info safe.
Understanding Network Computer Connections
Network computer connections are key to modern work setups. They let devices share resources easily. This turns single computers into team hubs.
What Are Shared Network Resources?
Shared network resources are digital items everyone can use at once. They save time and keep things the same everywhere.
Types of Shareable Resources
There are many things you can share on a network:
- File storage systems and directories
- Network-attached printers and scanners
- External drives and backup systems
- Applications and software licences
- Internet connections and bandwidth
Common Use Cases for Network Sharing
Network sharing helps a lot in work settings. It lets teams work on the same documents at the same time. Everyone gets the latest info from one place.
Printers for many users save time. Installing software for everyone at once is easier than doing it one by one.
Benefits of Accessing Network Computers
Using network computers has big advantages. Cost reduction is a big one because you share hardware.
It makes teamwork better, no matter where you are. Keeping data in one place makes it safer and easier to back up.
It also grows with your business without needing a whole new setup. These benefits make work more efficient and productive.
Common Network Types and Protocols
There are many network types, each with its own way of sharing. Knowing these helps pick the best for your needs.
SMB/CIFS Protocol Overview
The SMB protocol is for sharing files in Windows. IBM started it, and Microsoft made it better as CIFS.
It lets apps read and write files on other servers. It also handles user login, file sharing, and more.
NFS and Other Sharing Protocols
NFS is for Unix and Linux, letting users see remote files as local. Sun Microsystems created it.
Other protocols like AFP for macOS and FTP for the internet also exist. Each has its own strengths for different systems and needs.
These protocols are the base for easy access to resources across different networks. Companies choose based on their setup and needs.
Prerequisites for Network Access
Before we can connect to other computers on a network, we need to set up some basics. These basics make sure we can access shared resources smoothly and safely. Let’s look at what’s needed for good network connectivity.
Essential Hardware Requirements
Having the right network hardware is key. Without it, even the best software won’t work. It’s like trying to build a house without a foundation.
Network Interface Cards and Cabling
Every device needs a Network Interface Card (NIC) to connect to the network. Most computers come with Ethernet ports for wired connections. Laptops and mobile devices usually have wireless options too.
For wired connections, you’ll need the right cables. Cat5e or Cat6 Ethernet cables work well for most offices. Make sure cables are properly connected and tested for signal quality.

Network routers manage traffic between networks. Switches handle communication within one network. Small offices might use a combined router-switch unit. But bigger places need separate, more powerful devices.
Think about how much data you’ll be moving when choosing your equipment. Devices that can handle gigabit speeds are best for big files and videos.
Network Configuration Checklist
After setting up your hardware, you need to configure it right. This means setting up addresses and organizing your network.
IP Address Configuration
Getting your IP configuration right is key for network communication. You can use DHCP for automatic addresses or static addresses for servers and printers.
DHCP makes managing addresses easy, but servers and printers need static IP addresses. This keeps them accessible all the time.
Workgroup or Domain Setup
Choosing between a workgroup and a domain depends on your network size and security needs. Workgroups are good for small, simple networks.
Bigger places need domains for better security and management. A well-set-up workgroup or domain makes accessing resources easy.
Permission and Security Considerations
Security is vital to protect your network and devices from unauthorized access. Setting up the right permissions ensures users can only access what they should.
User Account Requirements
Each user needs the right credentials to access the network. In workgroups, users must have matching accounts with the same password on both computers.
Domains make this easier with central authentication. Make sure users have the right permissions to access resources without risking security.
Share Permission Levels
Understanding share permissions is crucial for controlling access. Permissions can range from read-only to full control, depending on what users need.
It’s best to give users the least necessary permissions. Use both share permissions and NTFS permissions on Windows for extra security.
Keep checking and updating permissions to keep your network safe. This ensures security while meeting changing user needs and organizational changes.
How to Connect to Network Computer on Windows
To connect to a network computer on Windows, you need to set up your network right. You also need to know how to share files and folders. This guide will help you do all this while keeping your network safe.
Configuring Network Discovery Settings
Setting up network discovery is key to connecting computers. Without it, other devices won’t show up on your network.
Enabling Network Discovery in Control Panel
First, open the Control Panel from the Start menu. Go to Network and Internet, then Network and Sharing Centre. Click Change advanced sharing settings from the left menu.
Look for the network profile section (usually set to Private). Expand it and choose Turn on network discovery. Also, pick “Turn on automatic setup of network-connected devices” for better performance.
Setting Up File and Printer Sharing
In the same advanced sharing settings, turn on file and printer sharing. This lets other computers see your shared stuff. You can also enable public folder sharing for more options.
For extra security, use password-protected sharing. This limits access to only those with the right login details on your computer or domain.
Accessing Shared Folders via File Explorer
File Explorer is the easiest way to find network resources. It’s a built-in Windows tool that makes finding and connecting to resources simple.
Browsing Network Computers
Open File Explorer and click Network in the left pane. Windows will show all computers on your network. It might take a bit to find all devices.
If some computers don’t show up, try using the UNC path. Just type \\computername in File Explorer’s address bar, replacing “computername” with the actual device name.
Navigating Shared Directories
Double-click any computer to see its shared folders and printers. Windows might ask for login details. Enter the correct username and password when asked.
Once connected, you can access and use the shared resources. You can open, copy, or edit files based on your permissions.
Mapping Network Drives for Permanent Access
Mapped network drives give you permanent access to resources. This means you don’t have to keep logging in and finding the same resources over and over.
Drive Letter Assignment Process
Right-click This PC in File Explorer and choose Map network drive. Pick a drive letter from the dropdown menu. Make sure it’s not one already used by a physical drive on your system.
In the Folder field, enter the path to the network resource you want to access. Use the format \\computername\sharename for the best connection. The Browse button can help if you’re not sure of the path.
Reconnection at Logon Options
Check the Reconnect at sign-in box for automatic reconnection at startup. This keeps your mapped drives available every time you log in.
The Connect using different credentials option lets you use different login details. This is handy if your Windows login is different from what the target computer needs.
| Connection Method | Best Use Case | Persistence | Authentication Required |
|---|---|---|---|
| Network Browser | Occasional access | No | Yes |
| UNC Path Entry | Direct access | No | Yes |
| Mapped Drive | Frequent access | Yes | Yes |
| Public Folder | Simple sharing | Varies | Optional |
Getting a Windows network connection right is all about setting things up correctly and having the right permissions. Always check your company’s security rules before sharing resources.
Accessing Network Resources on macOS
Apple’s macOS makes it easy to connect to networks. It has built-in tools for this. You can connect to shared resources in local networks or across wider areas.
Connecting Through Finder
Finder is the main tool for finding and accessing network resources. It’s easy to use, especially for those who like a visual approach.
Network Section Navigation
In Finder, go to the Network section in the sidebar. It shows devices and shared resources on your local network. The system finds compatible servers and workstations for you.
Double-click on any computer to see its shared folders and files. The interface makes it easy to find what you need. You can browse like you would local directories, but access is based on permissions.
Authentication Dialogue Handling
When you try to access protected resources, macOS asks for your login details. You have three main options:
- Guest access for public shares that don’t need login details
- Registered User for domain or local account login
- Using Apple Account for services that use Apple ID
For domain accounts, use the format domain\username. For local accounts, use \username. Make sure to type correctly, as some systems are case-sensitive.
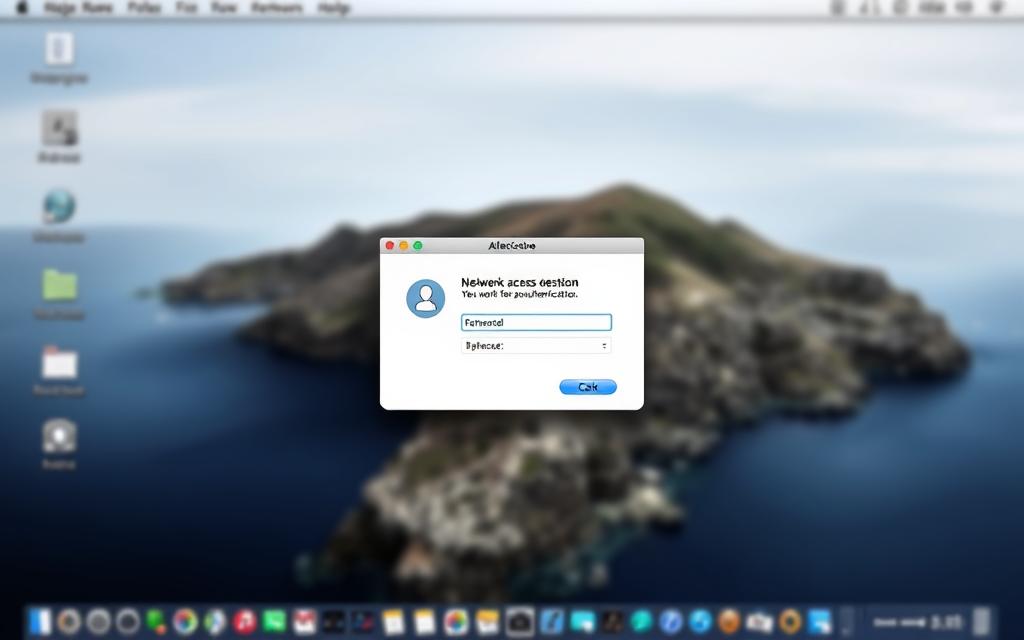
Using Connect to Server Feature
The Connect to Server feature lets you directly access network resources by address. It’s great for resources not found through network browsing.
Server Address Formatting
For successful connections, use the right address format. Start with smb:// for Windows shares. Then add the server name and share path. For example, smb://server.name/sharename or smb://192.168.1.100/sharedfolder.
Be precise with your syntax, including forward slashes and avoiding spaces in share names. You can use DNS names or IP addresses, but DNS names are more reliable in dynamic environments.
Connection Protocol Selection
macOS supports different network protocols. SMB is the most common for Windows. AFP is for older Mac servers, and WebDAV is for web-based shares.
Choose your protocol based on these factors:
- SMB is best for cross-platform compatibility
- AFP might be faster with older Mac servers
- WebDAV is good for cloud or internet-accessible resources
Mounting Network Volumes
Mounted network volumes show up as local drives in Finder. This makes it easy to access often-used resources without reconnecting every time.
Volume Management Techniques
Manage mounted volumes in Finder’s sidebar or on your desktop. Use the eject icon or right-click menus to disconnect properly. Improper disconnection can cause problems when reconnecting.
Check the volume icons in Finder for connection status. Dimmed icons mean there’s a problem, while normal icons show you’re connected. Always check your connections, especially during long work sessions.
Automount Configuration
Make frequently used volumes mount automatically at login in System Preferences. Go to Users & Groups → Login Items to add volumes to connect at sign-in.
For more advanced settings, use command-line tools like automount or edit /etc/auto_master. These need admin access but offer more options for businesses.
Remember, automounted volumes need the network to be available at startup. Consider adding delays or retries for unreliable networks.
Mobile Device Network Access
Modern mobile devices have changed how we access networks. Smartphones and tablets offer strong connectivity, keeping us productive on the go. But, they also bring unique security and compatibility needs.
Connecting from iOS Devices
Apple’s iOS supports network access through the Files app. To connect to SMB servers, tap the three-dot menu and choose “Connect to Server”. Just enter the server address in the format smb://server.name.
You’ll need valid login details from your network admin to connect. Once in, you can browse, download, and upload files on your iPhone or iPad. While iOS supports most file operations, some network setups might have limits.
“Mobile access to network resources represents the next evolution in workplace flexibility, allowing professionals to maintain productivity regardless of location.”
Accessing Shares from Android
Android devices offer flexible Android file sharing through various apps. The built-in Files app has network browsing under “Network storage”. You can add SMB, FTP, or SFTP server connections, depending on your device and Android version.
Third-party apps like ES File Explorer and Solid Explorer add more network features. They often let you bookmark frequent connections for easy access to important resources.
Recommended Mobile Applications
Several mobile network apps improve iOS and Android’s native features. FileBrowser for iOS adds advanced SMB functionality with support for multiple connections. It has a user-friendly interface for business users.
CX File Explorer on Android offers full network access with cloud storage. It supports SMBv1 to v3 and has media streaming. Documents by Readdle works well on both platforms, offering great network features.
These apps usually have extra security like encrypted connections and password protection. They also sync files for offline access. Always check if the app meets your network’s specific needs and security standards.
Security Best Practices
It’s vital to have strong security when using shared networks. This keeps your data safe and keeps systems working well on all devices.

Network Security Measures
Good network protection needs many layers. These layers work together to stop bad access and let good traffic through.
Firewall Configuration
A good firewall is your first defence. It checks network traffic against set rules. For the best firewall setup, follow these tips:
- Enable stateful inspection to track active connections
- Create specific rules for necessary services only
- Block all unnecessary ports by default
- Implement application-aware filtering where possible
Update your firewall rules often. This keeps up with new network needs and threats.
Encryption Recommendations
Encryption keeps data safe when it’s moving or sitting still. Modern encryption makes data unreadable if it’s caught.
Try these encryption methods:
- Use WPA3 for wireless network encryption
- Implement TLS 1.3 for all network communications
- Enable BitLocker or similar full-disk encryption solutions
- Utilise VPN technology for remote access scenarios
Access Control Strategies
Who gets to see what is key to network security. Good access management stops bad people from getting to sensitive stuff.
Principle of Least Privilege
This idea says users should only have access they need. It helps stop damage from mistakes or bad actions.
Here’s how to do it:
- Create role-based access control groups
- Regularly review user access requirements
- Implement temporary access for special projects
- Use separate accounts for administrative tasks
Regular Permission Audits
Checking access rights often is important. It helps find and fix too much access that’s not needed.
Make a plan for audits with these parts:
| Audit Frequency | Scope | Responsible Party | Documentation Requirements |
|---|---|---|---|
| Quarterly | Administrative accounts | Network administrators | Change log with justification |
| Bi-annually | User access rights | Department managers | Access matrix review |
| Annually | Service accounts | Security team | Usage analysis report |
These network security best practices are crucial. They help keep your network safe and working well against new threats.
Troubleshooting Common Connection Issues
Users often face problems when trying to connect to network resources. This can slow down work and make things less productive. We’ll look at common issues and how to fix them to get back to work smoothly.

Resolving Authentication Problems
Most often, users can’t get into the network because of authentication issues. These problems usually come from wrong passwords, expired login details, or setup mistakes.
Credential Management Solutions
Windows asks for login details when you try to access certain resources. Make sure to use the right format: domain\username for domain accounts or \username for local ones. The credential manager tool helps keep these details safe, so you don’t have to keep entering them.
If you keep getting asked for login details, try clearing them in Windows’ credential manager. This will make Windows ask for your login again, which can solve problems with passwords or permissions.
Fixing Network Discovery Failures
When computers don’t show up in network lists, it’s usually because of service problems. Network discovery needs several Windows services to work right.
Service Dependency Checks
Important services must be running for network visibility. Check if these services are active:
- Function Discovery Provider Host
- Function Discovery Resource Publication
- SSDP Discovery
- UPnP Device Host
Open services.msc to check these services. Make sure they start automatically. Restarting them often fixes the problem.
Addressing Permission Errors
Even with the right login details, permission issues can block access. These problems usually come from mismatched permissions at different levels.
Share vs NTFS Permission Conflicts
When share and NTFS permissions clash, Windows follows the stricter one. If you can’t access something despite having share permissions, check the NTFS permissions. The effective permissions tool in Windows security properties can help see what’s blocking you.
Inheritance and Propagation Issues
Permission inheritance problems happen when subfolders don’t get the right permissions from their parents. If you need special permissions for a subdirectory, break the inheritance. Use security advanced settings to make sure permissions are right across folders.
Changing permissions might need you to log in again. Always disconnect and reconnect after making changes to permissions.
Conclusion
Understanding both hardware and software is key to effective network access. This summary covers the main steps for sharing resources across different platforms.
Setting up your network correctly is crucial. Windows users need to enable network discovery and map drives. macOS users can use Finder and Connect to Server. Mobile devices offer access through special apps.
Keeping your data safe is important. Use strong passwords and access controls to prevent unwanted access. Troubleshooting helps fix issues and keeps your connection stable.
This recap shows how different systems share resources. Each has its own way but follows basic networking rules. Knowing these basics makes navigating any network easier.
For more on network basics, check out this guide on computer networking basics. It helps users set up secure, efficient connections on various devices and systems.
FAQ
What are shared network resources?
Shared network resources are files, folders, printers, or drives that can be accessed by others over a network. They help with teamwork, keeping data in one place, and using resources efficiently across different systems.
What hardware is required to connect to a network computer?
You need a Network Interface Card (NIC) in each device. Also, you’ll need Ethernet or fibre optic cables. Don’t forget routers and switches to manage the network.
How do I configure network discovery on Windows?
Go to Control Panel > Network and Sharing Centre > Advanced sharing settings. Turn on network discovery and file and printer sharing. This makes your computer visible on the network.
What is the process for mapping a network drive in Windows?
Open File Explorer and right-click on ‘This PC’. Choose ‘Map network drive’. Pick a drive letter and enter the folder path using UNC format. Select ‘Reconnect at sign-in’ for easy access. Click ‘Finish’ to finish.
How can I access a network share from a macOS device?
Open Finder and click ‘Network’ in the sidebar to find computers. Or, use ‘Connect to Server’ (Cmd + K) and enter the server address. Then, enter your login details when asked.
Are there mobile apps for accessing network shares on iOS or Android?
Yes, apps like FileBrowser for iOS and Solid Explorer for Android let you access network shares. They support SMB and other protocols for file management on your mobile.
What security measures should I implement for network sharing?
Use firewalls to control traffic. Encrypt data and set strong access controls. Regularly check user permissions to keep your network safe.
How do I troubleshoot authentication issues when accessing a network resource?
Make sure your username and password are correct. Check your permissions on the shared resource. Also, ensure the authentication protocol is supported and set up right.
What should I do if network discovery is not working on my Windows PC?
Check if network discovery services are running. Make sure your network profile is set to Private. Also, ensure ports are open in the firewall and all devices are on the same workgroup or domain.
Why might I encounter permission errors even after being granted access?
Permission errors can come from share and NTFS permissions not matching. Make sure your account has direct access. Also, check for deny entries that might block allowed permissions.
What protocols are commonly used for network resource sharing?
Server Message Block (SMB) is used in Windows, while Network File System (NFS) is for Unix-like systems. Both allow sharing files and printers across networks, with SMB being widely supported.
Can I automate mounting network volumes on macOS?
Yes, add the network share to your login items in System Preferences > Users & Groups > Login Items. Or, use scripts or tools like automount for automatic connection at startup.